The Future of Security: Exploring the Latest Fads in Electronic Protection Technologies
Digital safety and security technologies have ended up being progressively sophisticated, offering innovative options to address the ever-growing obstacles encountered by people and companies alike. From biometric verification to the integration of synthetic intelligence and maker learning, these fads hold the assurance of enhancing safety and security measures in extraordinary methods.
Surge of Biometric Authentication
With the enhancing demand for secure and practical authentication approaches, the surge of biometric verification has actually changed the way individuals accessibility and protect their sensitive information. Biometric authentication uses distinct biological features such as fingerprints, facial functions, iris patterns, voice acknowledgment, and even behavioral qualities for identification confirmation. This modern technology supplies a more reliable and safe and secure technique compared to standard passwords or PINs, as biometric information is incredibly hard to reproduce or swipe.
Among the crucial advantages of biometric verification is its comfort. Users no more need to bear in mind complex passwords or worry concerning shedding access as a result of forgotten qualifications. By simply using a part of their body for verification, individuals can quickly and safely gain access to their devices, accounts, or physical areas.
Additionally, biometric authentication enhances security by supplying a much more robust defense versus unapproved access. With biometric pens being unique per individual, the danger of identity theft or unapproved entrance is significantly reduced. This increased degree of protection is specifically vital in fields such as finance, health care, and federal government where securing sensitive info is paramount.
Integration of AI and Artificial Intelligence
The advancement of digital security modern technologies, exhibited by the surge of biometric verification, has led the way for developments in the integration of AI and Maker Discovering for enhanced recognition and security devices. By leveraging AI algorithms and Artificial intelligence versions, digital safety and security systems can now evaluate huge amounts of information to identify patterns, anomalies, and potential dangers in real-time. These technologies can adjust to advancing protection risks and offer aggressive feedbacks to mitigate dangers properly.
One considerable application of AI and Artificial intelligence in electronic safety remains in predictive analytics, where historical information is used to forecast possible protection breaches or cyber-attacks. This positive method permits protection systems to prepare for and protect against dangers prior to they take place, boosting overall precaution. Additionally, AI-powered surveillance systems can intelligently keep track of and evaluate video clip feeds to recognize suspicious tasks or people, boosting response times and minimizing false alarm systems.
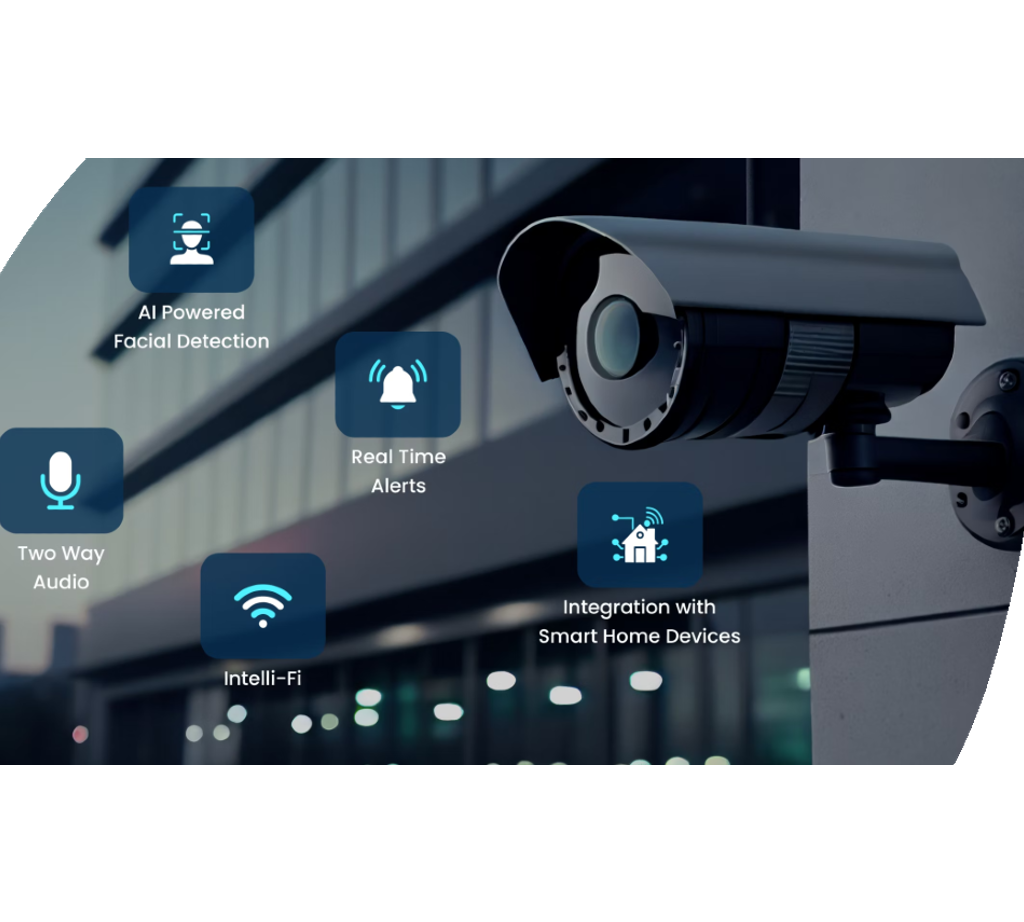
IoT and Smart Safety And Security Instruments
Improvements in digital safety and security innovations have brought about the emergence of IoT and Smart Security Instruments, changing the way safety systems run. The Internet of Points (IoT) has actually enabled safety and security tools to be adjoined and from another location obtainable, offering enhanced surveillance and control abilities. Smart Safety And Security Devices, such as clever electronic cameras, door locks, and activity sensing units, are outfitted with capabilities like real-time informs, two-way communication, and assimilation with various other clever home systems.
One of the significant benefits of IoT and Smart Security Instruments is the capacity to offer individuals with seamless accessibility to their safety systems with smart devices or other internet-connected tools. This comfort allows for remote tracking, arming, and deactivating of security systems from anywhere, offering home owners with comfort and adaptability. In addition, these tools typically incorporate innovative features like facial acknowledgment, geofencing, and task pattern recognition to boost overall safety levels.
As IoT proceeds to progress, the integration of fabricated knowledge and artificial intelligence algorithms right into Smart Safety Instruments is anticipated to additional enhance discovery accuracy and modification choices, making digital safety systems a lot more reliable and reputable.
Cloud-Based Security Solutions
Becoming an essential element of contemporary electronic security infrastructure, Cloud-Based Safety Solutions offer unmatched adaptability and scalability in securing digital assets. By leveraging the power of cloud computer, these services provide companies with innovative safety features without the need for comprehensive on-premises hardware or framework. Cloud-based security services make it possible for remote tracking, real-time signals, and systematized monitoring of protection systems from any area with a web connection. This not just enhances benefit yet also enables fast responses to safety and security occurrences.
Moreover, cloud-based protection options provide automated software application updates and upkeep, making certain that safety systems are always updated with the current defenses versus emerging threats. The scalability of cloud-based remedies allows companies to easily increase their security framework as required, accommodating growth and adjustments in safety and security demands. Furthermore, cloud-based safety and security solutions usually feature built-in redundancy and calamity healing abilities, decreasing the risk of information loss or system downtime. In general, cloud-based safety services represent an economical and efficient way for services to improve their security stance and protect their electronic assets.
Focus on Cybersecurity Procedures
With the enhancing elegance of cyber dangers, businesses are placing a critical concentrate on bolstering their cybersecurity steps. BQT Solutions. As technology developments, so do the techniques utilized by cybercriminals to breach systems and swipe sensitive information. This has triggered companies to spend heavily in cybersecurity measures to shield their information, networks, and systems from malicious attacks
Among the crucial trends in cybersecurity is the adoption of Read Full Report sophisticated file encryption methods to guard data both at remainder and en route. Encryption assists to make sure that also if data is intercepted, it continues to be unreadable and secure. Furthermore, the execution of multi-factor verification has become progressively usual to include an additional layer of security and verify the identities of customers accessing sensitive info.

Verdict